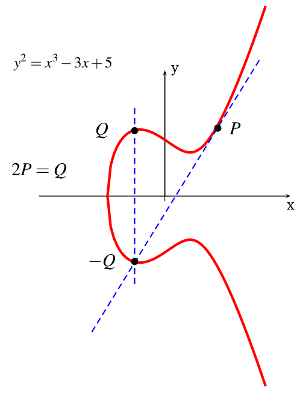
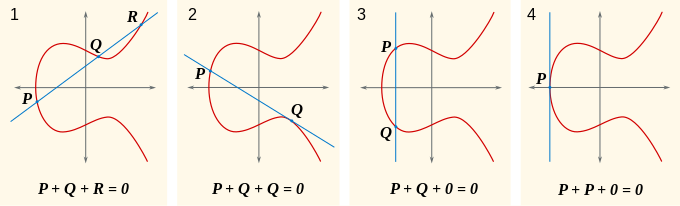
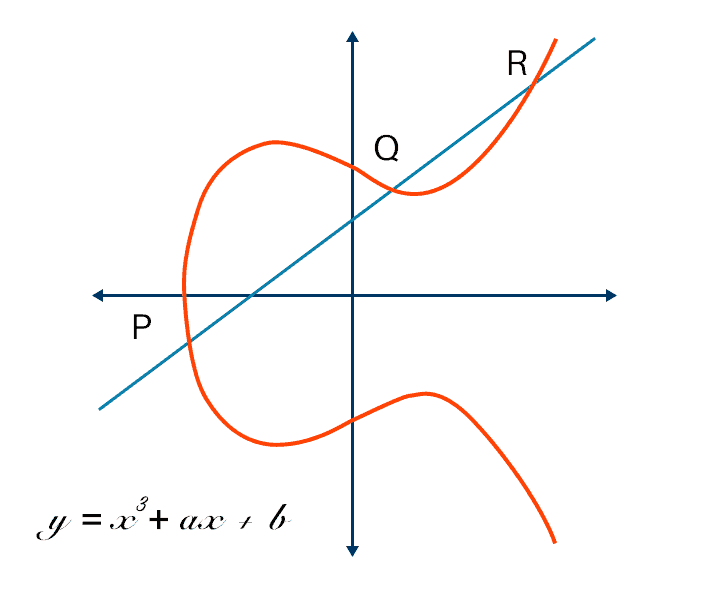SOLVED: Given an elliptic curve E over Zzg and the base point P = (8,10): E:y2 =.+4r+20 mod 29. Calculate the following point multiplication k P using the Double-and-Add algo- rithm. Provide

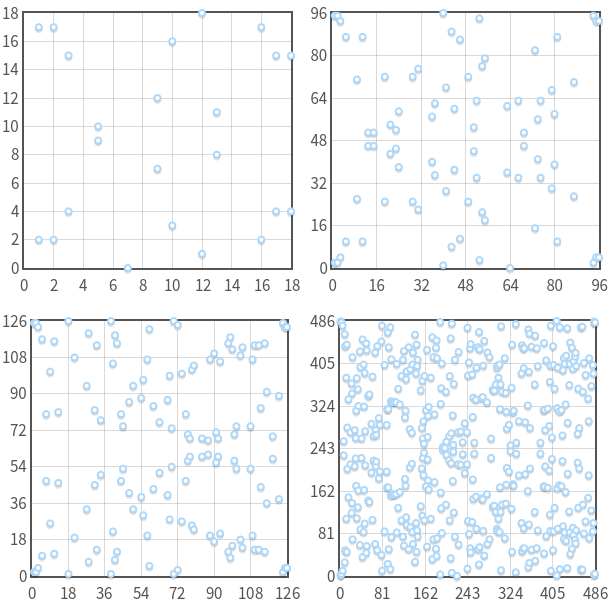
Picking a Base Point in ECC. In ECC, we have an equation of… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

Picking a Base Point in ECC. In ECC, we have an equation of… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
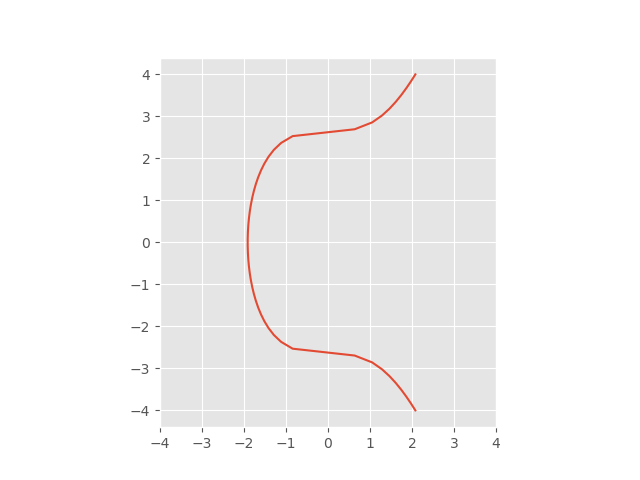
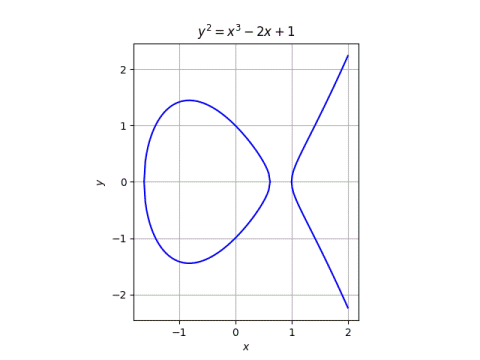
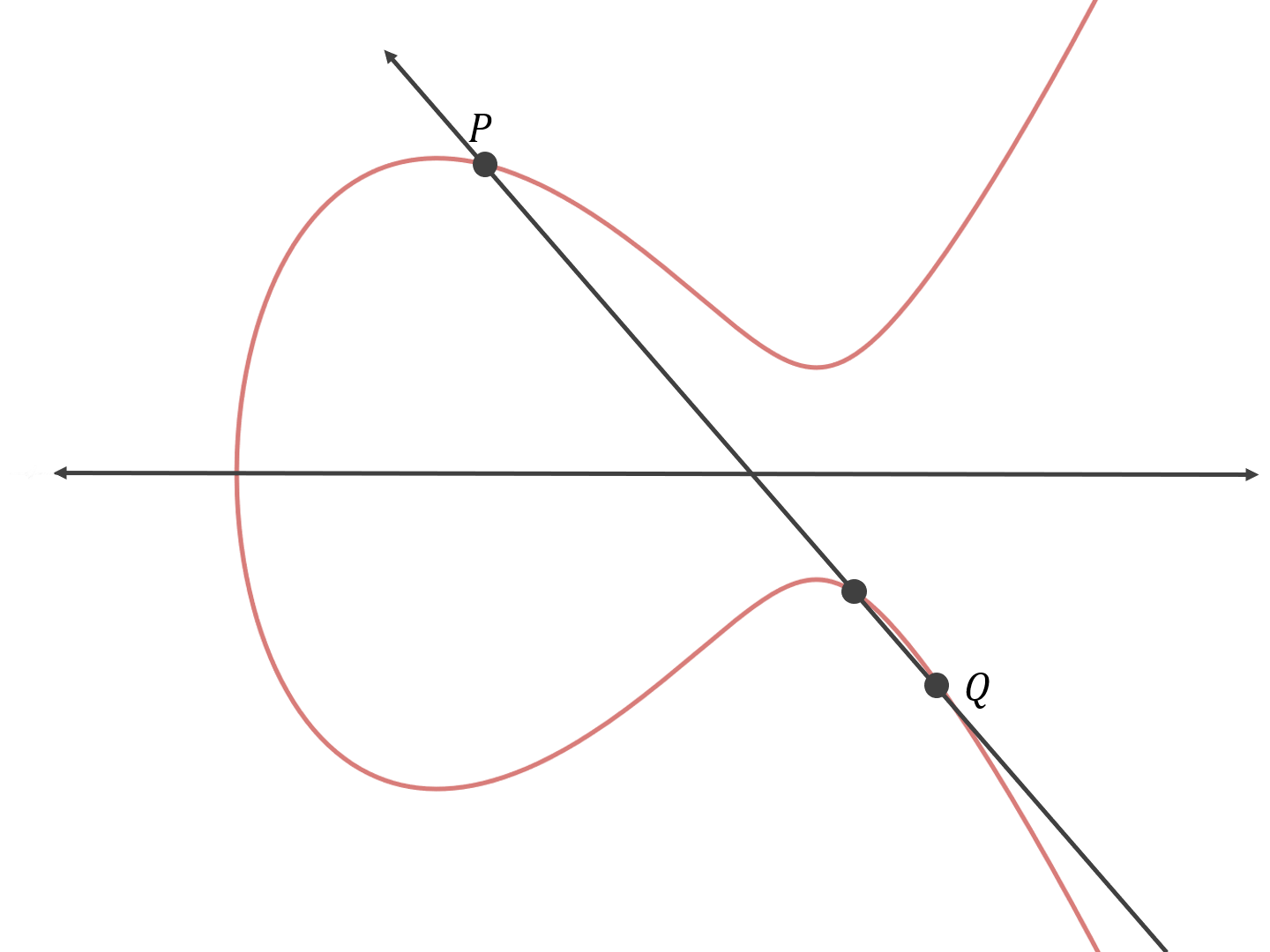
Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves
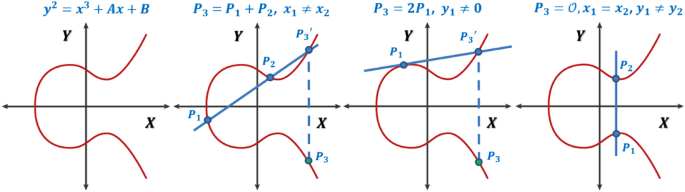
A generalized framework for elliptic curves based PRNG and its utilization in image encryption | Scientific Reports
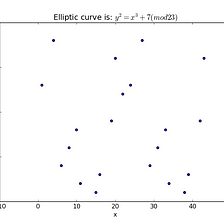
Picking a Base Point in ECC. In ECC, we have an equation of… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium